Chris Sereno
I am making significant changes to this site. Thank you for your patience.
Using file sets in Wireshark is a great feature. It allows for quickly navigating between smaller files instead of experiencing sluggish performance when analyzing one large file. However, there are times when packet captures were taken using a system other than Wireshark (such as TCPDump or Dumpcap). Other times someone else performs the captures and uses a different naming convention. Either way, there are times when it would be nice to convert these names into Wireshark’s file set naming convention.
While the general rule of thumb is to capture at the client, or at least start there, sometimes it’s necessary to take captures at both ends of a connection. The client perspective will allow you to view the problem as it is seen from the client. The server perspective might show the same thing. Or, in some cases like this one, it will provide the reason for the problem.
The problem was that a webpage wouldn’t load.
Everyone has that junk email account from an old mail service they don’t use anymore (ehem…AOL). They give it to salesmen, questionable websites, contests, fake accounts, etc. That way the majority of SPAM goes to the secondary account and fewer personal details are provided. While is a great solution, it’s time to upgrade to junk mail 2.0. I know you’re thinking, “Why? That just sounds like putting lipstick on a pig.
In order to understand application performance across the network, we first have to understand the basic mechanisms. In this case that foundation is built on TCP, and, more specifically, the built-in TCP Performance Options. There are many things that can be done in an application to improve performance. There are also several options from a network perspective, and more still in the operating systems. However, these all rely on the underlying protocol.
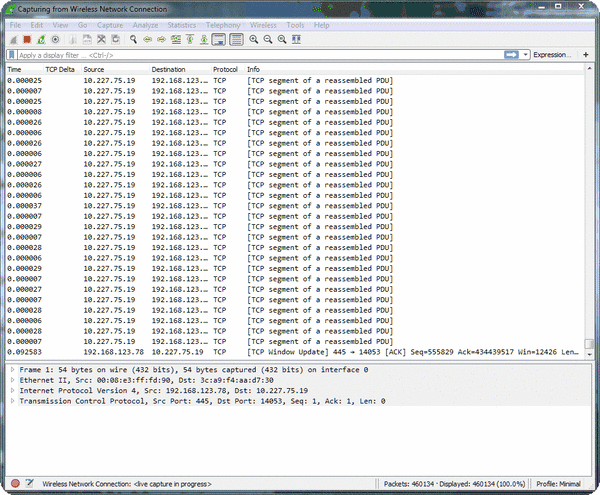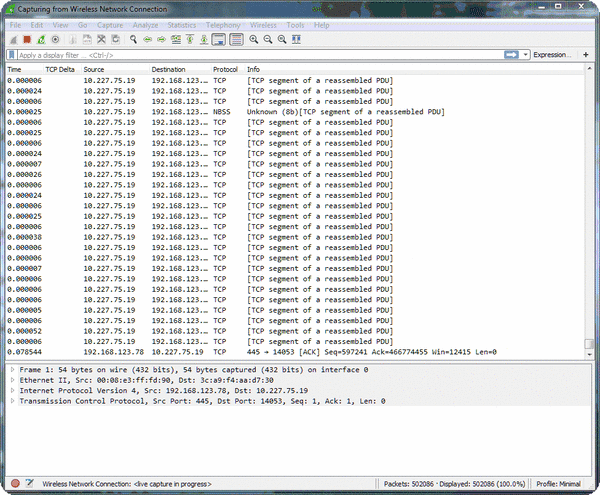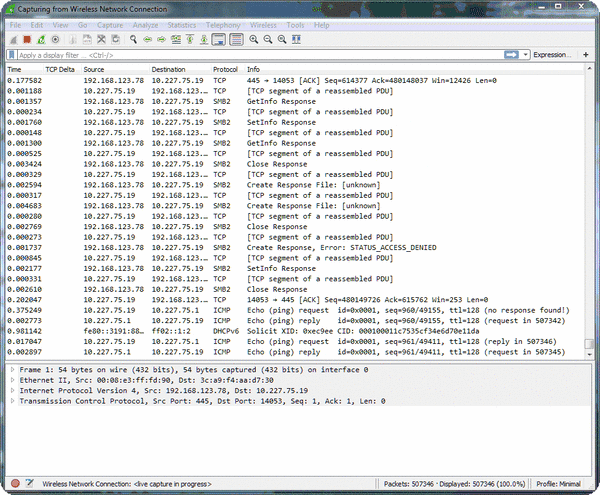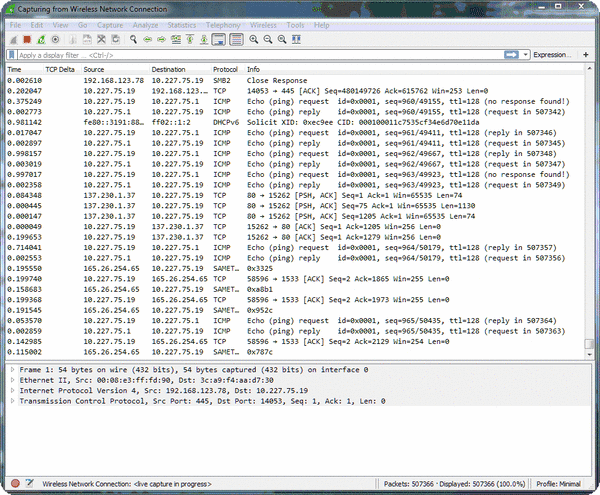
Start the Capture Now that you’ve decided where to capture, and you’ve prepared your interfaces and filters, you are ready to perform the capture. All you have to do at this point is hit the start button or double-click the interface in the list. There are usually multiple interfaces listed, so make sure you know which one you are wanting to use. Generally, this may be indicated by a small moving graph to the right of the device name indicating there is traffic present (the screen shot below currently show no traffic as I was in a lull).
It doesn’t matter if you just have a couple of word documents and pictures, or if you run a personal small business with important financial records; data backups are important. I’m sure we have all lost files we would do anything to get back. If not, you know someone who has. The world today is even more aggressive than before. Not only do we have to worry about hard drive failures, data corruption, and accidental deletions, but now we have ransomware and other malicious attacks attempting to access, control, and hold our data hostage.
 Chris Sereno
Chris Sereno