Chris Sereno
I am making significant changes to this site. Thank you for your patience.
You may have heard the term “Every Day Carry (EDC)” from self-defense or survival circles. That is where I first heard it. As a tech guy, I think this same term can be applied to the gear we techies carry on a daily basis. So, I wanted to provide a quick list of the things I carry daily to/from work and elsewhere. These may not help you survive a zombie apocalypse (whatever that is), nuclear fallout, or a foreign invasion, but they should help make your day-to-day life a little easier.
Packet captures give us a very detailed and in-depth look at network traffic. They can be used to establish baselines, discover network devices, diagnose application and performance issues, or identify security threats. The previous post described what packets are and their function at a high level. It also gave an overview of the process used to capture them. Once you have identified your purpose for performing a capture, you can begin preparing for it.
I have had several family members and friends lose access to their social media accounts, have malicious emails sent from their address, and even succumb to ransomware. The nature of these “hacks” or “attacks” varies widely, so there isn’t a “one-size-fits-all” solution. But, even though there are many ways to break into a house, doesn’t mean we don’t lock our doors or leave the key in the mailbox for everyone to use.
Do you ever wish you could control what appears on your screen at all times when surfing the net? Do you ever get distracted or pulled to another site, article, or game only to forget what you intended to do in the first place? Well, you can take back some of the control and your productivity in one easy step: by installing an ad blocker.
Some of the best ad blockers go beyond just ads, but actually block other elements of web pages designed to pull your information or run extra scripts and more.
How do you go about catching the one of the fastest things known to man (light) at a specific point in time with pinpoint accuracy over and over again? With a little patience and your network card, of course! This post is an introduction to the process of capturing network traffic (aka “sniffing” or “tracing”). With most of my blog being dedicated to network performance analysis, a post like this is foundational, and will help you understand the basics moving forward if you are new to “sniffing the wire”.
*Disclaimer: all captures in this post were anonymized using TraceWrangler.
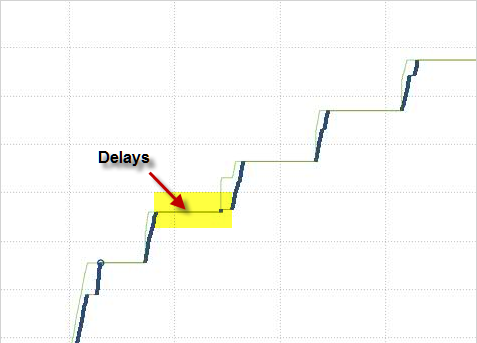
I was recently asked to help with a performance issue. I was informed a transfer was going to take weeks instead of a couple days as expected. The transfer rate was getting 80Mbps throughput max on a 10Gbps connection. So, I setup captures at both ends and got to work. This is just a quick summary of that work with the classic tell-tale signs of a performance problem.
 Chris Sereno
Chris Sereno