Packet Threat Analysis
Everyone needs to do some housekeeping at different points, and I figured it was time I did some a basic security sweep of my setup. To get started, I performed a quick packet capture on the very server that hosts this blog. I decided to give one of CloudShark‘s newer and more distinct features a spin with my recently created account; their Threat Assessment tool. I thought it would be interesting to pit this against PacketTotal as well. These are both great tools with similar, but also different purposes. At the time, I had SSH and web ports open along with a few other unused ports for various common services. The only true security measure in place was a few basic iptables rules.
CloudShark
What I Liked:
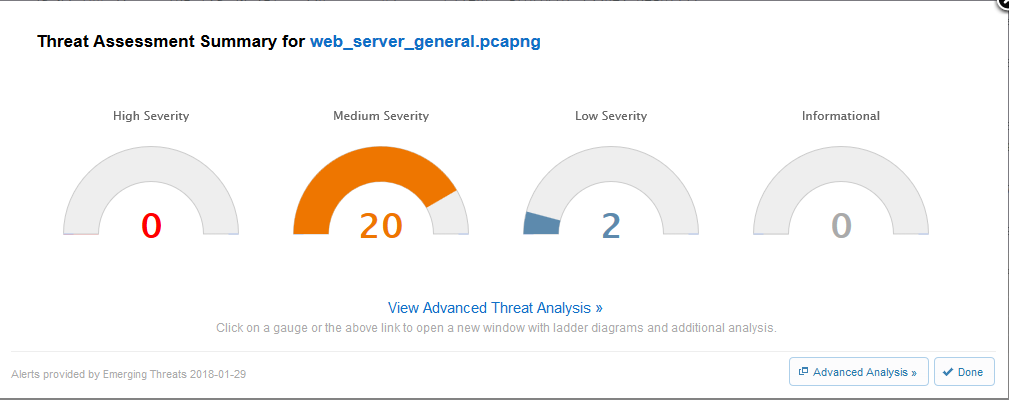
- Up front, quick severity level rating dashboard
- Brief descriptions of issues which helps puts everything in laymen’s terms
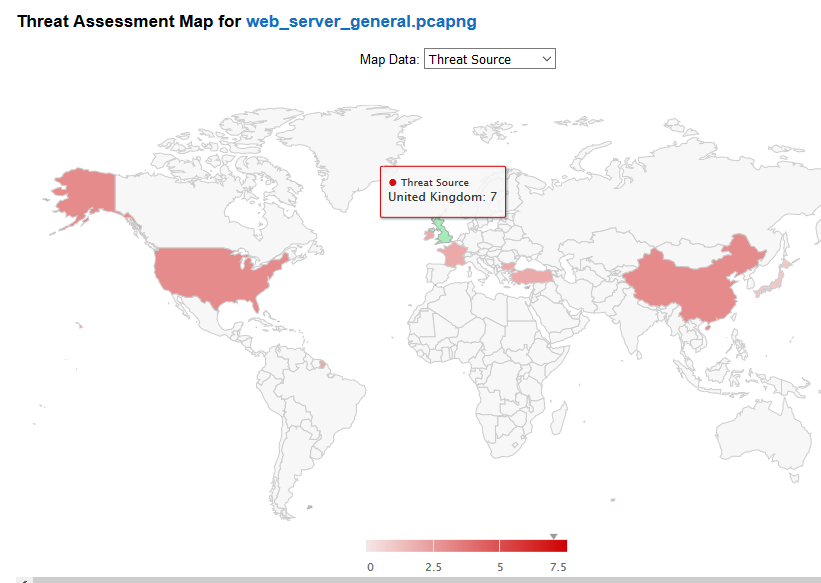
- World map view
- Privacy settings
- External references to source data and additional information
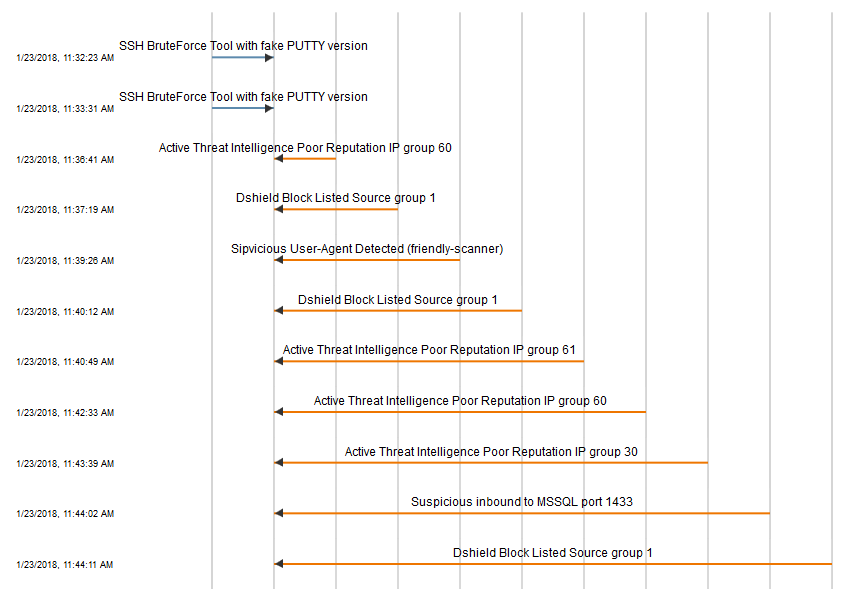
- Ability to view the actual packets
- Ability to separate views into new windows and share specific links (or embed the graphs into this website)
- Ability to create your own charts and incorporate other existing CloudShark features.
- Not having to run WireShark with vulnerable dissectors locally with possible malicious content.
What I Didn’t Like:
- Not much focus on WHO attacks are coming from beyond their IP address and country, but only on the technical threats. On one hand this is good and doesn’t lead to “wild goose chases.” On the other hand, I like to know everything I can about a potential threat.
- Limited scope – This assessment is very good at what is does, but there is a lot of technical detail withheld from the reports. Again, most of the information can be found in the packets themselves, but it would be awesome to have the data rolled up in these charts.
- The statistics menu took a long time to process. Clicked on it again was fast, but with no information displayed. I’ll have to give this another shot sometime.
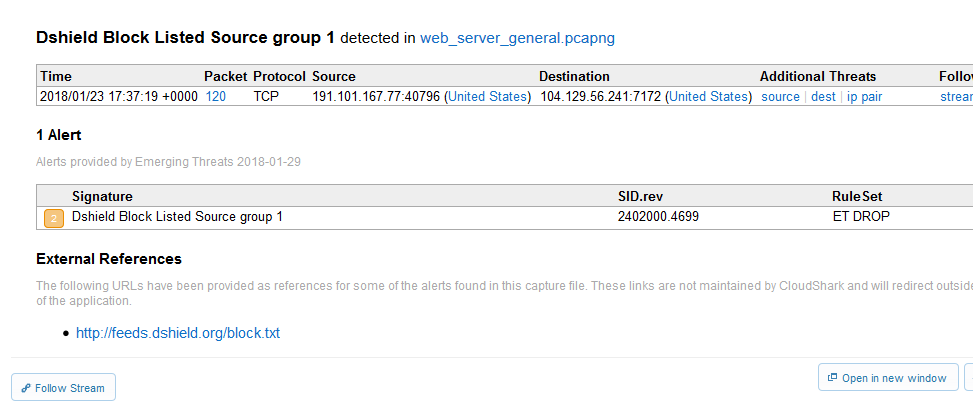
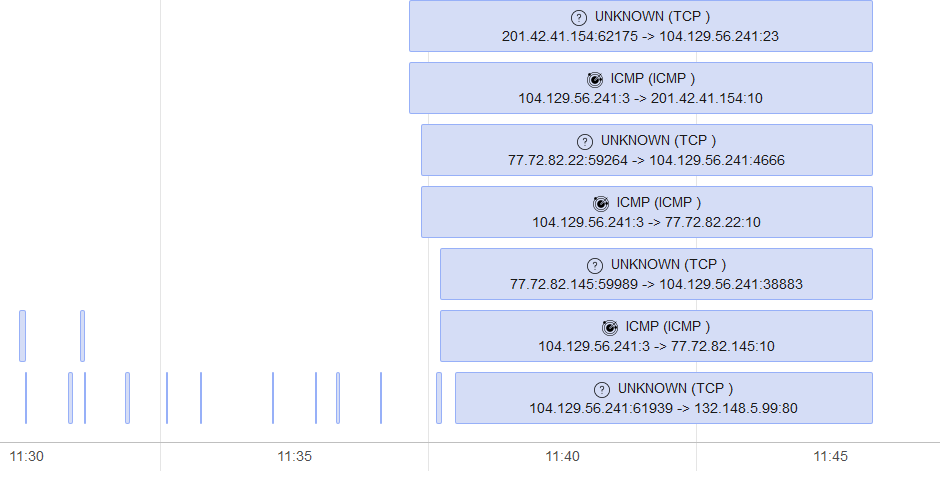
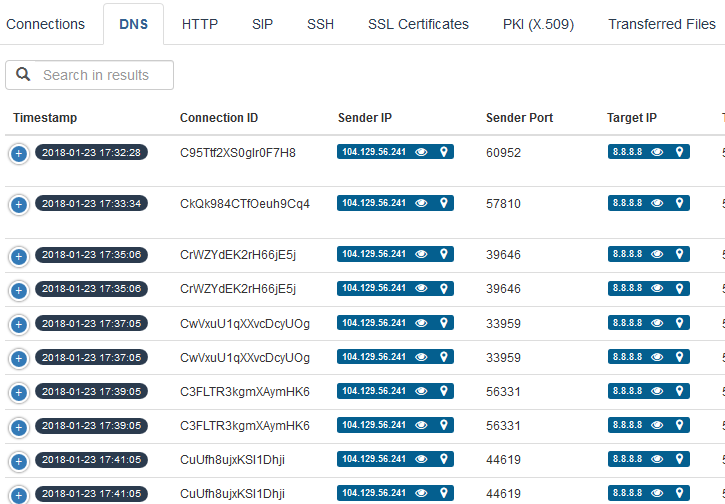
Screen Shots
PacketTotal
What I Liked:
- Breakdown by protocol
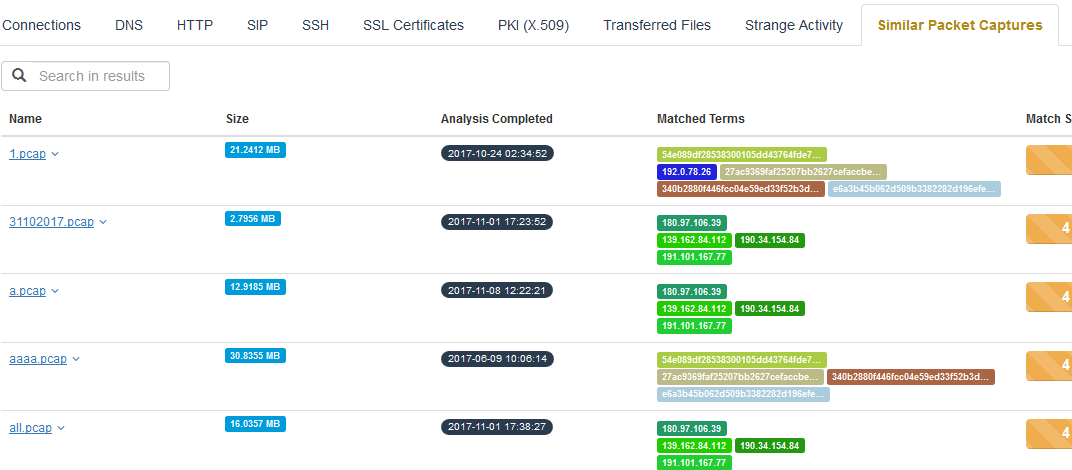
- Ability to reference similar captures as this is a public packet repository. That is great for tracking signatures and patterns
- WhoIS Info included
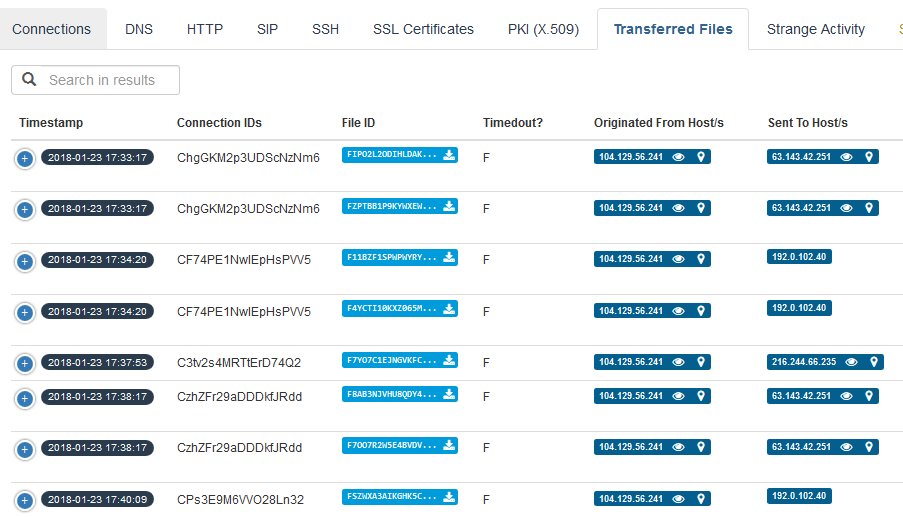
- Certificate and file listings
- Many great built-in graphs and charts for data visualization from a security perspective
- Free with no account necessary. It’s as anonymous as you make it
What I Didn’t Like:
- Not as private – potential for personal or more sensitive information to be made public if the uploaded captures aren’t carefully anonymized first.
- No packet view that I found, so you can’t get as hands on within the tool itself
- More granular interface requiring more clicks to get to the desired information
- Doesn’t having the backing and support of a business with full-time staff, so there is less support, fewer integrations, etc.
Screen Shots
Overall Impressions
Both of these tools gave me good insights as to what took place during the short captures I performed. I was able to identify some access and data transfer attempts. I could trace back attempts by region, obtain more details about the threats, and perform a quick triage. CloudShark’s Threat Assessment is a great addition to their suite of analysis features and makes their product even stronger and more competitive. It is something that will pull users in versus allowing them to stay in a traditional windowed application. PacketTotal has the “feel” of a tool that was made by a security analyst for a security analyst. It provides great detail quickly with good dashboards, but you do have to know what you’re looking at. No integration with other platforms means this is the perfect tool to complement an analysis suite. One could even use it alongside CloudShark without feeling too redundant.
 Chris Sereno
Chris Sereno