CloudShark 2018 Halloween Challenge

Well, Tom and the team at CloudShark have put together an excellent packet capture challenge on their blog once again. It has actually been awhile since I’ve dug into a capture due to my recent shift in focus to Amazon Web Services, so this was a lot of fun for me. I feel like once you’re a “packet junkie” you are always one!
<span style="color: #ff0000;">*SPOILER ALERT*</span> The rest of this post describes the challenge and the process I followed for solving the challenge. If you have not completed it and intend to do so please stop reading here.
The Challenge
This challenge essentially boiled down to exporting the shared capture file and then analyzing it to find 5 (or more) hidden pumpkins. My time is limited these days, so I found 5 and stopped there.
My Approach
I approached this challenge similar to how I handle most cases. I thought up a few possible scenarios that I could chase down quickly, a few more that could take some time, and decided after that I would fall back to a more structured approach if needed. I like to be efficient these days, so starting with the structured approach seemed like it might waste time. Please listen to what I say and not what I do 🙂
My Initial Ideas:
- An actual image of a pumpkin that was transferred as a file (quick)
- A pumpkin image found in the characters when following a stream (quick depending on #of streams)
- Decoding an SSL stream to find another streamed pumpkin (harder and longer)
- An animated gif or video of a pumpkin in a video stream (longer)
Pumpkin #1
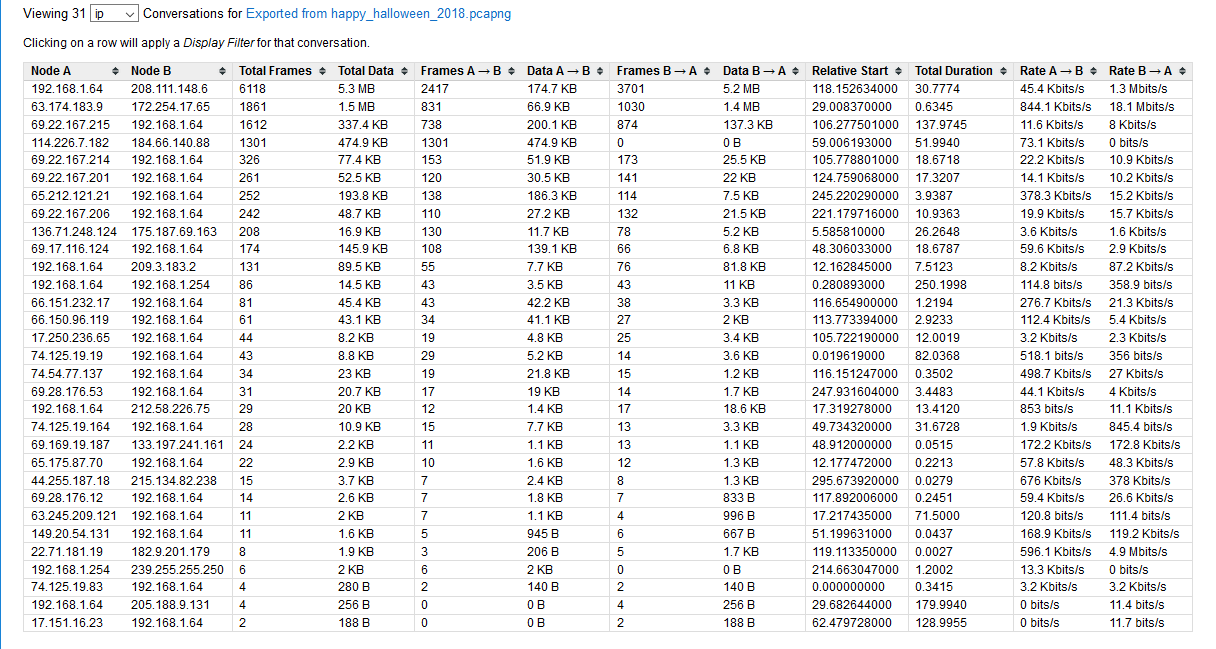
For the first pumpkin I went after my first idea. The first thing I did was look at the number of conversations in the file. As you can see, there are 31 streams. I decided I didn’t want to sift through all of that manually.
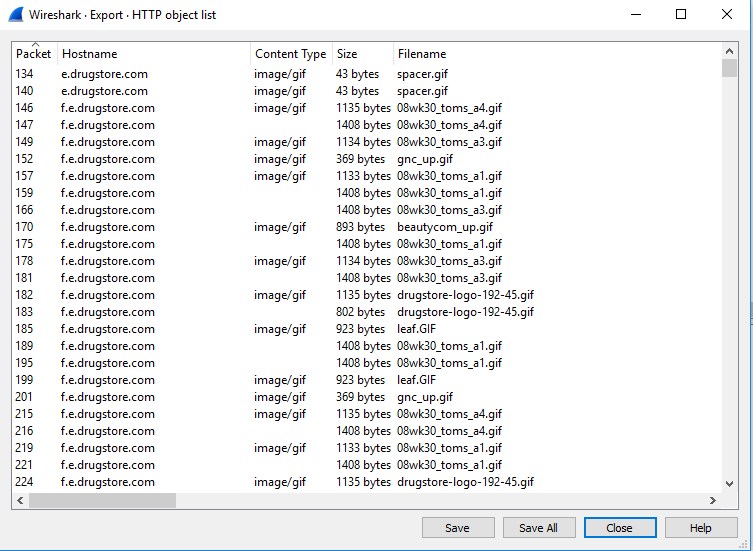
So, I think CloudShark is an amazing tool, and this post and others I’ve made are a testament to that. However, there are times when using a power drill is just faster than using a screw driver. I also didn’t see any rules stating I couldn’t use other tools. In fact, I specifically saw a statement to “think outside the gourd.” So, for pumpkin #1 I actually downloaded the file and used Wireshark to search for keywords such as “pumpkin,” “halloween,” “jpg,” etc. To my knowledge Wireshark is still better at performing string searches than CloudShark (feature request CloudShark 😉 ). To my surprise, I didn’t find the word “pumpkin.” What I did notice though was quite a few packets returned when searching for image files. This was unexpected, so I decided to use Wireshark’s “export object” feature to quickly double-check. That didn’t help much, because I saw a large list of returned image names. It looks like Tom figured this would be where everyone would start so he made it difficult (touché, Tom, touché).
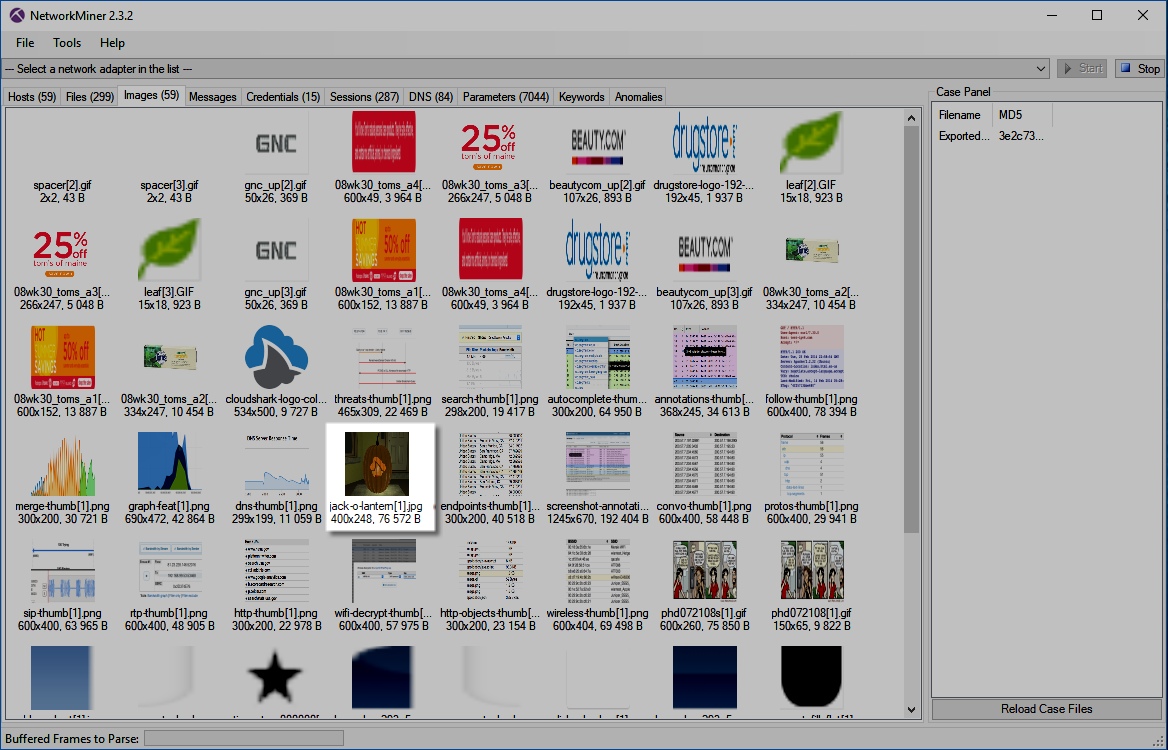
This “quick and easy” idea was turning out to be longer than I thought. Not to be dissuaded, I turned to an even better tool by Erik Hjelmvi called Network Miner. This tool is very good at extracting images from pcap files. I saved out the capture file as a pcap instead of pcapng, loaded it into NetworkMiner, navigated to the “Images” tab and had my first success. There before me was a beautiful image of a pumpkin with its name. I noticed Tom named this image “jack-o-lantern” instead of “pumpkin.” So far, Tom – 2 Chris – 0. Well played, sir, but now I’m onto you!
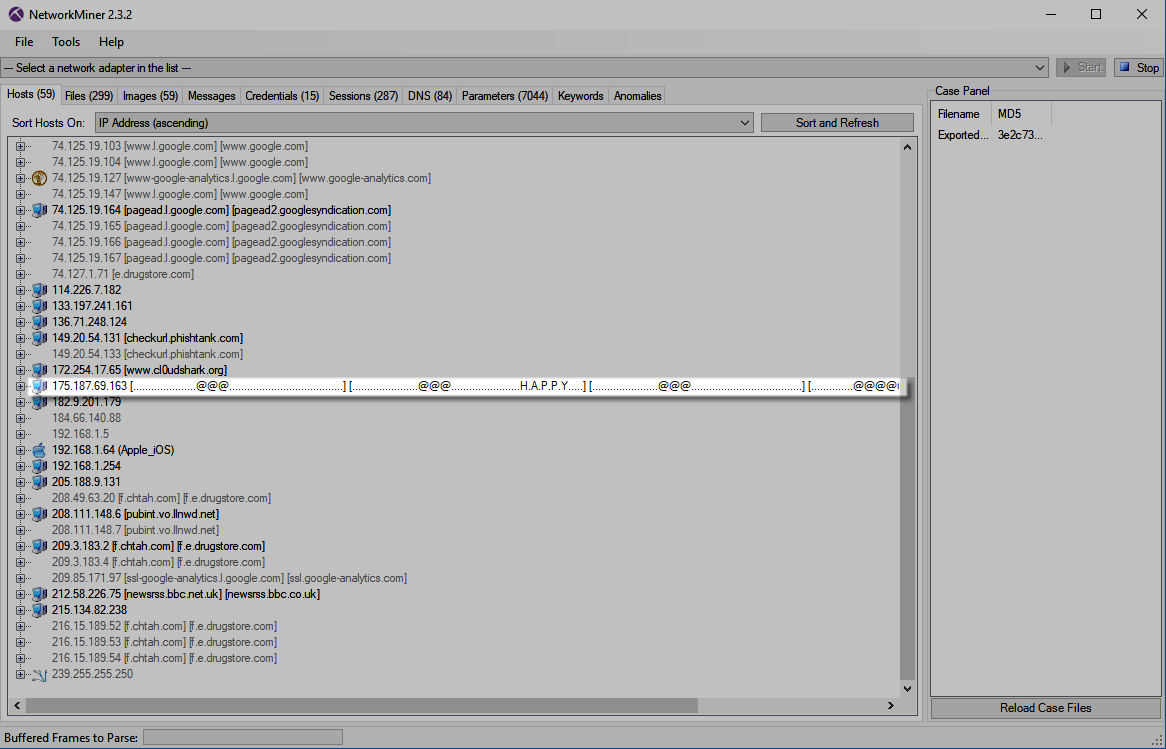
While I had NetworkMiner open, I just clicked through the tabs real quick to see if anything interesting was revealed. Sure enough, something caught my eye on the “Hosts” tab. I saw some interesting characters with the word “HAPPY.” I made a mental note of this and continued back to CloudShark to bag my first pumpkin.
Being that this is a CloudShark challenge, I had to find the view for this pumpkin in my browser with a link to share. Fortunately, the experts there have incorporated the “HTTP Object List” feature. As such, you can view the image directly in the packet capture by clicking here. Also, here is the packet containing the GET request.
Pumpkin #2
Whew! I learned a couple of lessons from Pumpkin #1. First, Tom is not messing around. Second, it isn’t really paying to use other tools for this as he is, for some unknown reason, trying to get us to use CloudShark’s built-in features. Going back to my note from NetworkMiner I decided to dig into the hosts field and find that message. When getting the HTTP Object List for Pumpkin #1, I also saw more weird symbols backing up this interesting find.
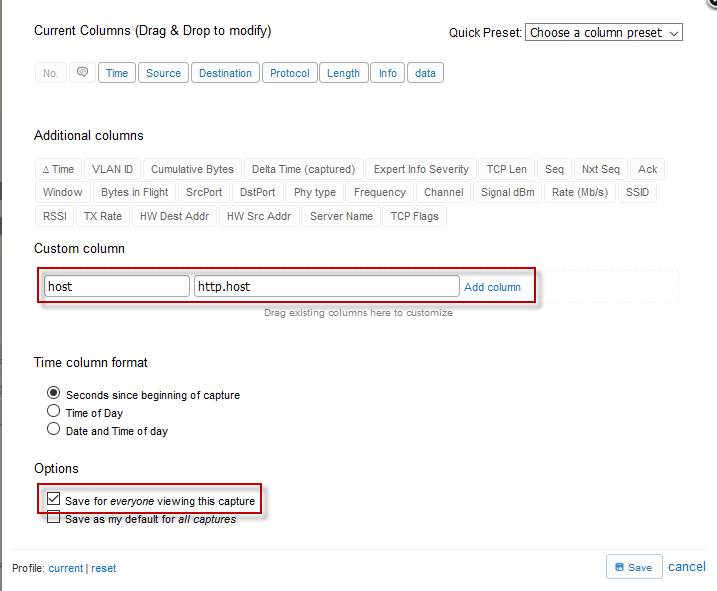
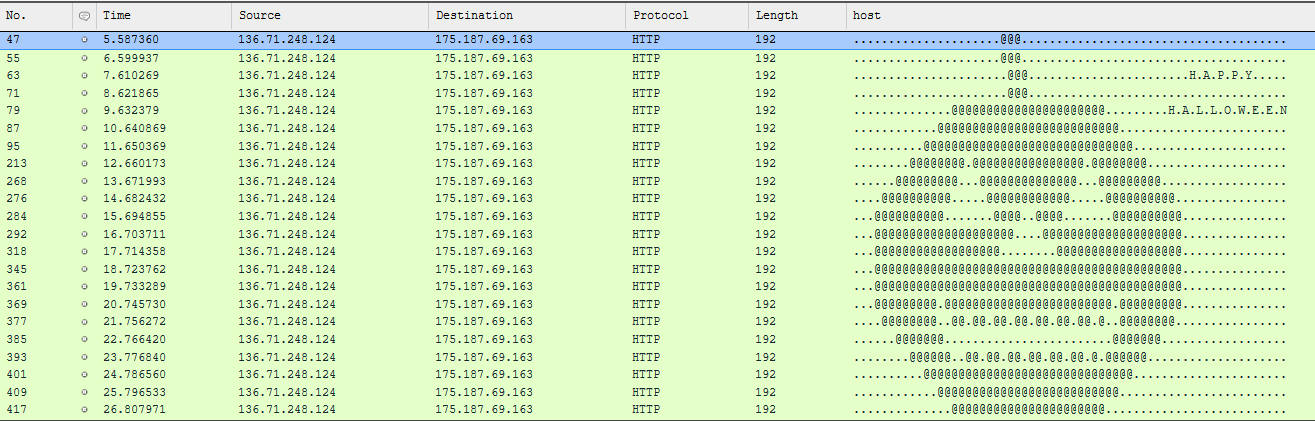
I just knew this was my next pumpkin, but the ASCII characters weren’t lining up. More than that, they were spread across streams. So, I can’t export another object or follow a stream to get this. Hmm? I pondered a bit and then decided to use the packet list itself as my tool of choice with a custom view. I went to the “Profile” button and clicked on “Custom Columns.” Here, I added an “http.host” column and saved it for everyone viewing this capture.
I then applied a filter for the IP address involved paired with its GET requests. Upon hitting “Apply” a beautiful ASCII pumpkin appeared before me. (Click the image or click here to view this directly in CloudShark).
Pumpkin #3
With Pumpkin #1 and #2 under my belt, I was feeling more confident. Going back to my idea list I decided to try to find a TCP stream and “follow” it. I hit another discouraging stat though. There are 286 TCP streams in this file. I decided to head back to Wireshark and use its “Follow TCP Stream” feature, because it has a nifty little button in the bottom-right corner of the stream window to change streams. So, I went through the streams 1 by 1 until I saw a pumpkin. Alas, I found it within TCP stream 88. View it below or click here.
Pumpkin #4
My confidence was quickly shattered. While pumpkins 1-3 took me a little while they weren’t all that difficult to find. Searching through the rest of the packet list I couldn’t find any other images or ASCII pumpkins or streams. Worse than that my other ideas turned up empty. There weren’t any RTP or voice streams. I also realized I didn’t have keys to decrypt the SSL traffic, so that was no good. I started pouring over the other CloudShark features and windows to see if anything turned up, but I didn’t have any luck. I decided to give it a rest and return the next day.
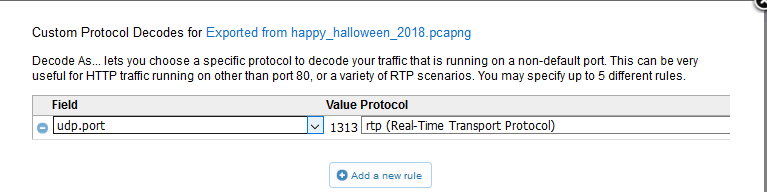
Well, the break and some sleep helped. I figured Tom was done playing nice and he wanted people to actually prove themselves worthy of taming this powerful cloudy beast. Every time I viewed the capture, I noticed some UDP packets that weren’t typical background chatter. There was an actual UDP stream with a lot of one-way communication. This had to be my next pumpkin. Not only that, it had to be a stream like I guessed. This drew my attention to CloudShark’s “Decode As” feature. I quickly added a new rule to decode this stream as RTP.
I then clicked “Analysis Tools” -> “RTP Streams” and was pleased to see a stream. Upon clicking the play button I heard a familiar voice from the movie “It’s the Great Pumpkin, Charlie Brown.” I’m not sure if this one directly counts, but it has the word “pumpkin” in the stream and refers to a pumpkin-based movie, so I counted it. You can listen to the stream below or click here.
Pumpkin #5
At last, I made it to the final pumpkin. I had no idea where this one could be though. There were so many distractions in this capture. I saw everything from CloudShark graphics to weather maps to album covers to more albums covers to even more (or “anal bum covers” to you Saturday Night Live Celebrity Jeopardy fans). I gave it another rest, because that seemed to work before. When I returned, I decided to look at the protocol hierarchy. I noticed an SMTP stream here. Could this be it, I thought? Did Tom hide another pumpkin in an email? I quickly clicked on it to view the stream. Sure enough, I saw a message in the email.
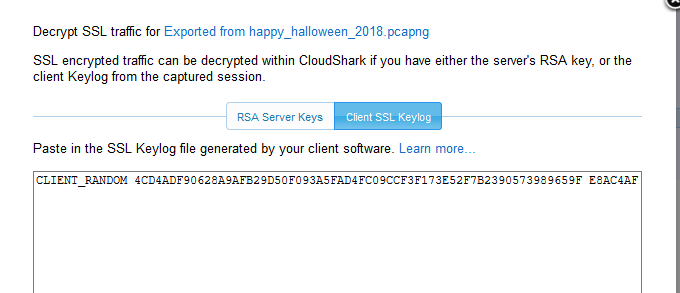
“Laurie! Michael has escaped the sanitarium and is in the house! Use this to find him:
CLIENT_RANDOM 4CD4ADF90628A9AFB29D50F093A5FAD4FC09CCF3F173E52F7B2390573989659F E8AC4AFFCDAD005F5ED4E29D2625A49378A25E7D5B85D5418AC51C1D0CC50B52B39DB3998C606202339178C1EA441CE0“
Well, another dead end I thought. I pondered this for a few minutes and decided this had to be a clue. No way would Tom go through the effort of including an SMTP stream with a hidden message for nothing. Or would he? I don’t actually know that much about him or this challenge. Maybe he likes creating more work for himself. I copied the message out and tried converting it to base64 and playing with it a few other ways. I couldn’t make heads or tails of it. Then I realized that I was overthinking it. This was not a hidden message. This was the tool to find him (as Tom clearly stated) and this is a CloudShark challenge…duh! This is a client SSL keylog! Could I use this to decrypt an HTTPS session? My pulse quickened as the thrill of the chase was coming to an end. Had I cracked the code and found the fifth pumpkin? I quickly pasted it into the “Client SSL Keylog” window.
I then proceeded to the packet list and used “ssl” as my filter. Thankfully, this revealed a shorter list of packets with one packet standing out from the others. It actually had decrypted data.
(Expand the “Line-based text data” to see the data)
Clearly, this is the 5th and final pumpkin, but it still was not in proper form. Apparently, Tom had one more trick up his sleeve. I knew what I had to do. I clicked “Follow HTTP” and there before me was my last pumpkin.
Click here to view it in all its splendor.
Thank you Team CloudShark for another great capture and several hours of fun!
To see my capture annotations (I only did a few) click here.
[UPDATE: CloudShark has posted the solution here. They included a link to this post. Thanks for the shout out!]
*Disclaimer: The featured jack-o-lantern image is from CloudShark and the capture file shared in this challenge. I did not create and do not own that image. I used it only to make a visual cue back to them.
 Chris Sereno
Chris Sereno